![]()
Updated: Sep.28, 2007
With the spread of the Internet as social infrastructure, computer security incidents*1, such as information leakages and unauthorized access, occur ever more frequently and their impact has been aggravated.
To cope with computer security incidents, technological capabilities are required to identify trends of unauthorized access, collect information and implement measures to prevent unauthorized access, and analyze the threat to information systems. In addition, a response structure to promptly handle new types of unauthorized access shall be developed. In the Internet world, organizations which deal with problems related to computer security - CSIRT*2(Computer Security Incident Response Team) - have been established at a country or company level to handle measures to protect information systems from computer security incidents.
Hitachi Group set up the HIRT (Hitachi Incident Response Team) in October 2004 as an organization to address computer security incidents. This team provides information on measures against vulnerability and incidents to all divisions in the Hitachi Group to assist in actions to protect customer systems from incidents such as unauthorized access.
The purpose is to contribute to achieving a safe and secure network environment for customers and society by preventing the occurrence of security incidents throughout the Hitachi Group and by taking prompt action against incidents that occur.
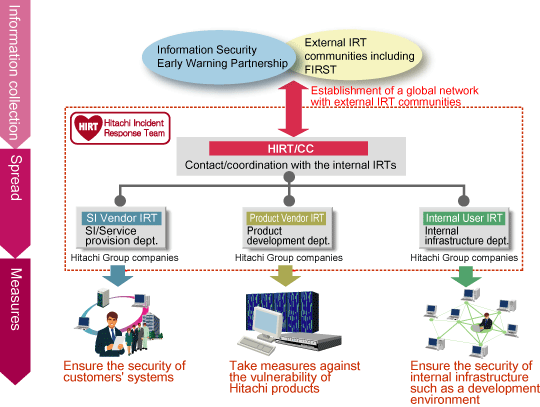
Currently, cooperative activities among organizations related to the network society are essential to promote countermeasures against vulnerability/incidents related to computer security and network. In Japan, there is a structure of vulnerability information distribution "Information Security Early Warning Partnership", which is one of the measures taken by the Ministry of Economy, Trade and Industry. This is a structure whereby software product developers, website operators, finders of vulnerability, IPA, which obtains vulnerability information, and JPCERT/CC, which is a coordination institution, properly distributes information on vulnerability found in software products and websites in a coordinated manner in order to control damages from unauthorized access to computers and computer viruses.
The response status of software product vulnerability is available on the portal site operated jointly by IPA and JPCERT/CC, "JVN (JP Vendor Status Notes)".
It seems that CSIRT recognition has increased little by little, but specific details such as "What is the incident response?" and "What kind of activities do they do?" may not be fully known. The concept of CSIRT activities remains somewhat vague and may be hard to understand. Therefore, we have prepared an animation illustrating the activities from security information collection to information distribution to internal IRTs, led by HIRT/CC in the above figure. We hope this will help you better understand our HIRT activities.
Sep.28, 2007 - Added announcement about removal of HIRT animation.
Jun. 22, 2007 - This webpage was newly created and released.
Prepared by:Umeki/HIRT,Okashita/HIRT, Onishi/HIRT