![]()
(JVN#06924191, JVNDB-2011-000064)
Last Updated: September 30, 2011
HIRT reports the vulnerabilities to JVN in line with the framework of vulnerability handling - Information Security Early Warning Partnership.
Microsoft Windows XP contains an issue when processing TCP packets, which may result in a denial-of-service (DoS).
Base Metrics: 4.3
Access Vector: Network
Access Complexity: Medium
Authentication: None
Confidentiality Impact: None
Integrity Impact: None
Availability Impact: Partial
Temporal Metrics 3.5 (August 19, 2011)
Exploitablity: Proof of concept code
Remediation Level: Temporary fix
Report Confidence: Confirmed
+ Windows XP
Potential packet flood denial of service (DoS) when malicious TCP packet is received. DoS may be converged autonomously in some cases such as Figure 1.
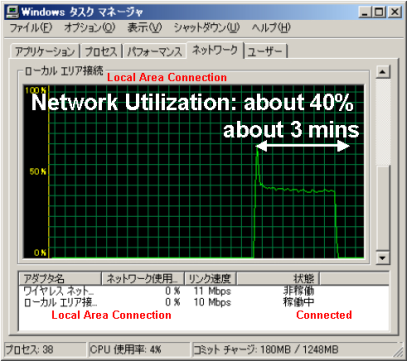
Figure 1: Experimental verification of this vulneravility (case of autonomous convergence).
The following workaround may mitigate the affects of this vulnerability.
+ Use a Microsoft Windows XP firewall or network firewall to limit access to affected ports.
[2009-09-21] Confirmation of this vulnerability in Microsoft Windows XP SP3.
[2009-09-25] Vulnerability reported to vendor.
[2010-06-07] Vendor Response (Vendor confirms this issue).
[2010-06-24] Notification to vendor about "Vulnerability report to JVN".
[2010-07-01] Vulnerability reported JVN in line with the Information Security Early Warning Partnership.
[2011-08-01] Coordinated public release.
Masato Terada (HIRT), Naoko Ohnishi (HIRT) and Hiroko Okashita