![]()
(VU#243585, JVNVU#99125992)
Last Updated: July 27, 2015
Some SSL/TLS implementations accept the use of an export-grade (512-bit or smaller) RSA public key in a non-export RSA key exchange ciphersuite. This flaw could allow an attacker able to act as a Man-in-The-Middle (MiTM) to downgrade algorithm such as an export-grade (512-bit or smaller) RSA key, obtain session keys, and decrypt SSL/TLS traffic. This vulnerability is commonly referred to as "FREAK" (Factoring Attack on RSA-EXPORT Keys).
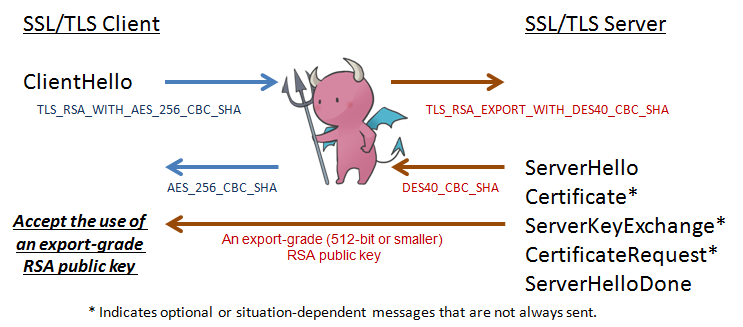
Figure 1. Man-in-The-Middle (MiTM) and algorithm downgrade.
The ServerKeyExchange message is sent by the server only when the ServerCertificate message does not contain enough data to allow the client to exchange a premaster secret such as RSA_EXPORT (if the public key in the server certificate is longer than 512 bits) key exchange methods. Also this ServerKeyExchange message conveys cryptographic information to allow the client to communicate the premaster secret: an export-grade (512-bit or smaller) RSA public key to encrypt the premaster secret with which the client can complete a key exchange. Some SSL/TLS implementations accept the use of this export-grade RSA public key.
+ SSL/TLS libraries and applications
An attacker able to act as a Man-in-The-Middle (MiTM) to downgrade SSL/TLS algorithm such as an export-grade (512-bit or smaller) RSA key, obtain session keys, and decrypt SSL/TLS traffic.
Configure server and client applications not to use export grade ciphersuites such as the followings. These ciphersuites use 512 bit RSA/DH in key exchange phase and 40 bit RC2/RC4/DES in session phase.
TLS_RSA_EXPORT_WITH_RC4_40_MD5 (0x0003)
TLS_RSA_EXPORT_WITH_RC2_CBC_40_MD5 (0x0006)
TLS_RSA_EXPORT_WITH_DES40_CBC_SHA (0x0008)
TLS_DH_DSS_EXPORT_WITH_DES40_CBC_SHA (0x000B)
TLS_DH_RSA_EXPORT_WITH_DES40_CBC_SHA (0x000E)
TLS_DHE_DSS_EXPORT_WITH_DES40_CBC_SHA (0x0011)
TLS_DHE_RSA_EXPORT_WITH_DES40_CBC_SHA (0x0014)
TLS_DH_anon_EXPORT_WITH_RC4_40_MD5 (0x0017)
TLS_DH_anon_EXPORT_WITH_DES40_CBC_SHA (0x0019)
Some SSL/TLS implementations accept the use of an export-grade (512-bit or smaller) RSA public key in key exchange phase, even when negotiated a non-export RSA key exchange ciphersuite.
Masato Terada (HIRT) and Naoko Ohnishi (HIRT)