![]()
Eradicating redirector websites (in Japan) for the Rig Exploit Kit
Last Update: April 24, 2017
Malware infections that use the Rig Exploit Kit (RIG - EK), such as infections with the ransomware CryLocker and the internet banking malware Gozi, have been around since around September 2016. Malware infections are performed by redirector websites (pages injected with malicious code) in Japan redirecting visitors to Rig Exploit Kit infector sites.
HIRT-PUB17003 introduces activities of the Japan Cybercrime Control Center (JC3), an organization of which Hitachi is now part, which are aimed at eradicating the redirector websites described above.
Figure 1 shows how malware infections are spread using the Rig Exploit Kit. If a user visits a website in which malicious code has been injected so that the user is redirected, the user might be redirected to a Rig Exploit Kit infector website, resulting in their computer becoming infected with malware. In some cases, the visitors' bank account information is stolen and then used in illegal money transfers via internet banking. Victims might also encounter ransomware attacks that encrypt and hold their data for ransom.
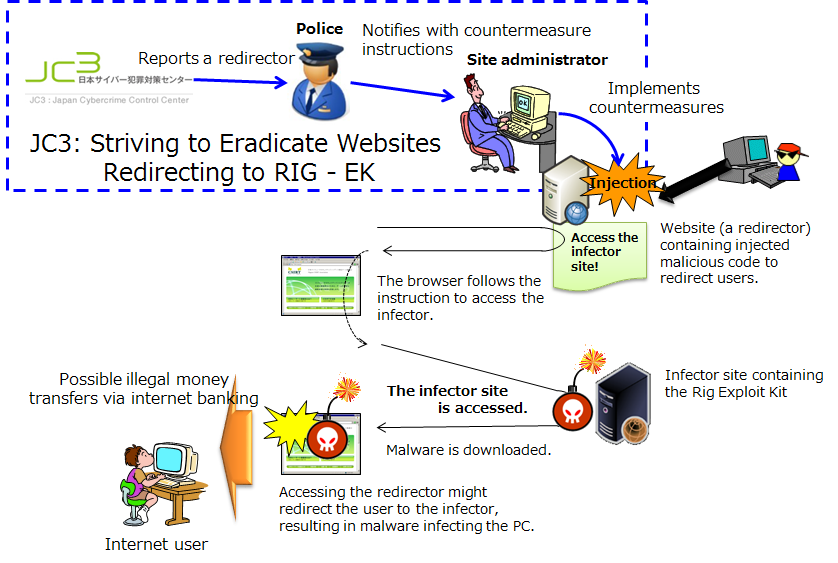
Figure 1: How malware infections are spread using the Rig Exploit Kit, and countermeasure approach by JC3
JC3 understands the mechanisms behind the spread of malware infections that use the Rig Exploit Kit. Companies involved in projects to analyze illegal money transfers and working groups for sharing threat information have taken great strides to accumulate information about redirectors in Japan. JC3 is working to recover websites injected with malicious code by RIG-EK (as shown by the dotted blue frame in Figure 1). As part of this ongoing effort, JC3 provides vital information to the police, and Japan's prefectural police instruct website administrators in how to recover websites that have been injected with malicious code in order to redirect users to infector sites. JC3 is working to uncover every aspect of cyber attacks.
If you are a website administrator, make sure that your website has not been injected with malicious code and does not redirect users. In addition, implement the following comprehensive security measures for your website.
If you use the Internet, install anti-virus software, update the definition file (virus pattern file) of the anti-virus software, and run virus scans regularly. Take proactive steps to protect against malware infections that use the Rig Exploit Kit, and update all software such as the OS (especially Windows OSs) used by your PC, the browser (especially Internet Explorer), the browser's plugins (especially Adobe Flash Player), and your software. Always keep these up-to-date.
Masato Terada (HIRT), Naoko Aasai (HIRT),Naoko Ohnishi (HIRT) and Tatsuya Sekiguchi (Hitachi Systems)