![]()
- Virtual experience demonstration (4) -
Last Update: April 09, 2018
Since the middle of May, the ransomware WannaCry has been active in the wild. WannaCry exploits a vulnerability in Windows SMBv1 (vulnerability CVE-2017-0145, addressed by security update MS17-010), which allows remote code execution. The ransomware spreads like a network worm to infect other Windows systems with this vulnerability. HIRT-PUB17009 introduces how network infection spreads to other vulnerable Windows systems.
Ransomware WannaCry (MD5: db349b97c37d22f5ea1d1841e3c89eb4) attempts to propagate itself by infecting other vulnerable Windows systems. Therefore, it (1) probes devices in the same network, and in parallel (2) probes the IP address space randomly. In the virtual experience demonstration, we will show how the ransomware infects other devices in the network by probing within the same network using a MP4 video file. To demonstrate the way in which the ransomware infects other devices in the network, we prepared one infected PC and six PCs on which measures against the relevant vulnerability (MS17-010 CVE-2017-0145) had not been taken (Figure. 1).
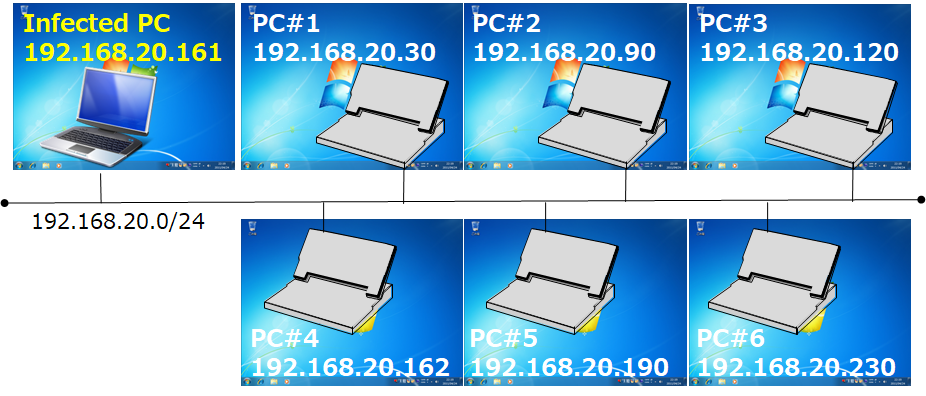
Figure 1: Network configuration for demonstrating network infection
The virtual experience demonstration of HIRT-PUB 17009 is four times speed MP4 video file, showing the infection at about four times the actual speed. In the video, six PCs become infected in about 90 seconds. In reality, this infection would take about five minutes.
Figure 2: Virtual experience demonstration of a WannaCry network infection (at four times speed)
The infected PC probes for PCs in the same network by continuously increasing the 4th octet of the IP address by one (in the case of the network configuration in Figure 1: 192.168.20.1, 192.168.20.2, ..., 192.168.20.254)(Figure 3). Furthermore, the infected PC probes (1) probes IP addresses in the same network as the infected PC, and in parallel (2) probes the IP address space randomly. This causes the sources of infection to rapidly increase, and causes the infection to spread (Figure 4).
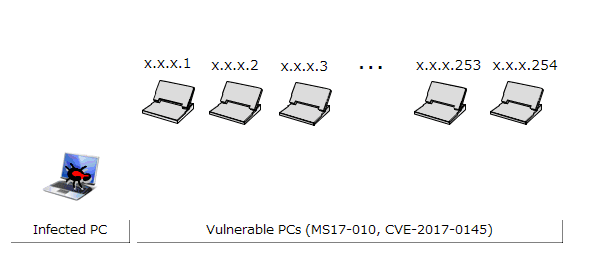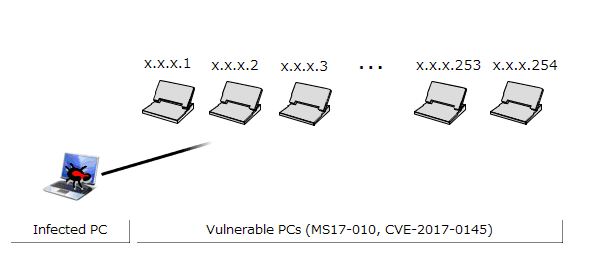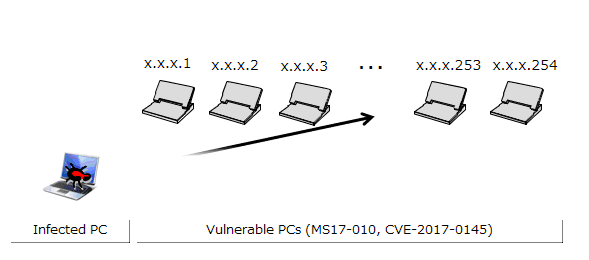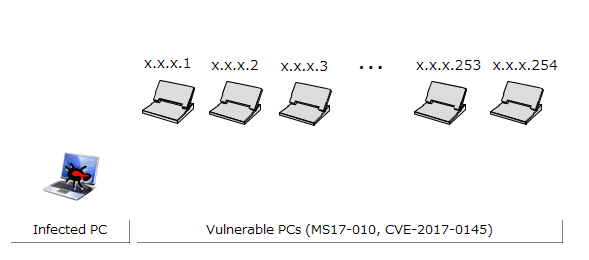
Figure 3: Diagram of probing within the same network
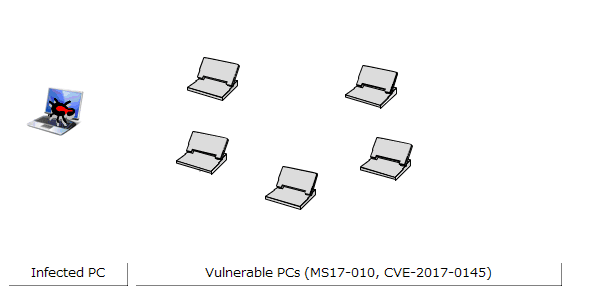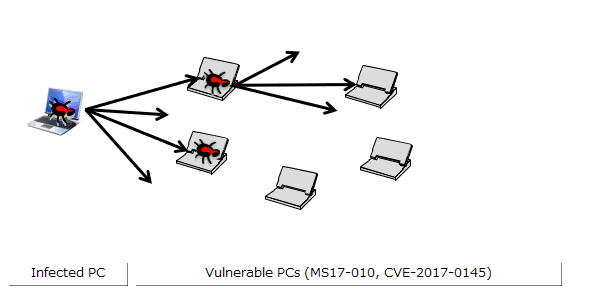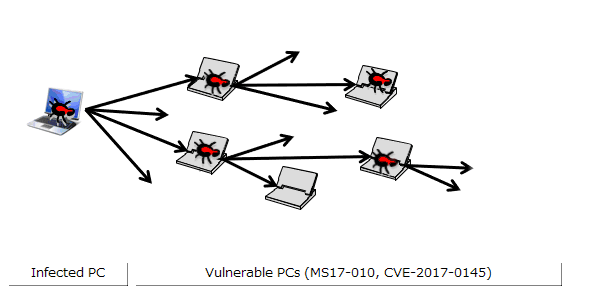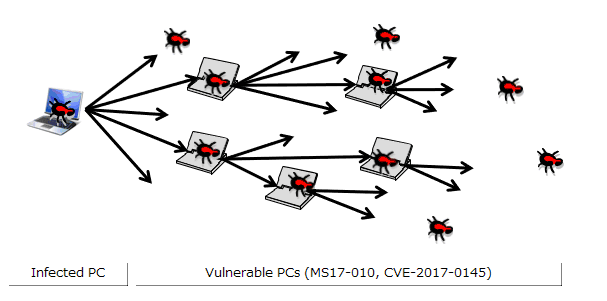
Figure 4: Diagram of self-propagation
Figure 5 shows the flow of infection shown in the virtual experience demonstration, leading to the infection of six PCs. Three groups as infection steps: {infected PC=>PC#3(120)}, {PC#3(120)=>PC#1(30), PC#2(90), PC#5)}, {PC#2(90)=>PC#4(162), PC#6(230)}. This part of the video is consistent with the rapid spread of infection due to the self- propagation shown in Figure 4, as well as the rapid increase in sources of infection.
Although infected PCs probe PCs in the same network by repeatedly increasing the 4th octet of the IP address by one, the actual order of infection is as follows: PC#3(120), PC#2(90), PC#1(30), PC#6(230), PC#4(162), PC#5(190). The infection does not necessarily spread in the order that IP addresses are probed. (The numbers in parentheses are the 4th octet of the IP address.)
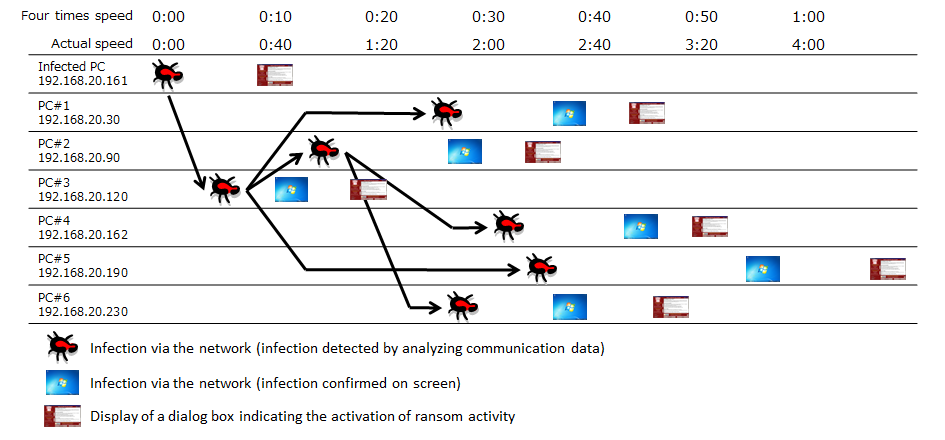
Figure 5: Flow of network infection in the virtual experience demonstration
Wannacry
SHA256:24d004a104d4d54034dbcffc2a4b19a11f39008a575aa614ea04703480b1022c
MD5:db349b97c37d22f5ea1d1841e3c89eb4
Masato Terada (HIRT), Naoko Asai (HIRT) and Naoko Ohnishi (HIRT)