With a shift to a zero-trust and internet-based architecture for IT infrastructure, the entire Hitachi Group will achieve a safe and secure IT environment for both its employees and businesses.
Business will expand through the introduction of new ways of working and the adoption of cloud services.
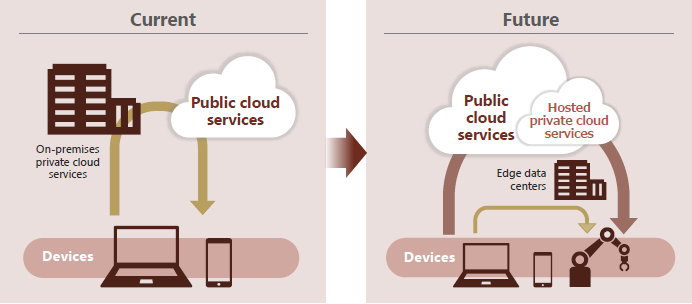
In response to trends such as sudden changes in business environments and workstyles as well as the promotion of DX#1 and data utilization, we are formulating strategies for cloud and edge computing that incorporate an expanded migration to public cloud services, support for multiple cloud environments, and the use of edge data centers, based on the prerequisite of a cloud-first and asset-light approach.
In parallel with promoting the shift to the cloud, we are promoting the introduction of security measures that are appropriate for hybrid on-premises/cloud environments.
We are migrating our IT infrastructures and applications to the cloud to streamline in-house IT assets. Additionally, we are leveraging advanced technologies and adopting globally standardized applications to swiftly respond to expansions in our business portfolio and other environmental changes.
To enable users to select the optimal cloud for their needs, we are promoting the development of a multi-cloud environment. By integrating various business applications on the multi-cloud platform and constructing workflows, we aim to contribute to increased operational productivity through standardizing and automating our business processes.
Furthermore, under the policies of “cloud-first” and “asset-light,” we are encouraging a mindset shift among employees to quickly master advanced technologies without waiting for the development of IT assets.
To accelerate DX in development environments and at manufacturing sites, we provide a platform that seamlessly connects edge devices such as PCs, smart devices, and IoT#2 devices with the cloud. To enable cloud usage and secure inter-site communication from business environments such as R&D or production and manufacturing, we establish secure virtual networks on the internet tailored for each business unit, realizing an optimal network adapted to zero trust.
Moreover, with the spread of 5G communication and the utilization of CPS#3, as well as AR#4/VR#5 and visualization for real-time processing, we are considering infrastructure improvements such as 5G environments and the use of low-latency edge data centers.